What is SASE? An In-depth Guide to Secure Access Service Edge
In the ever-evolving digital landscape, businesses face increasingly complex network environments. As organizations expand globally and adopt cloud-based resources, traditional network security measures struggle to keep pace. This is where Secure Access Service Edge (SASE) comes into play. This blog post explores the concept of the SASE meaning (pronounced “sassy”), its components, and why it is becoming an essential solution for modern businesses.
In recent years, network complexity has soared to unprecedented heights. The surge in remote work, mobile connectivity, and cloud innovations has made traditional perimeter-based network security models ineffective. Businesses are now searching for solutions that can cater to the dynamic access requirements of decentralized workforces while still ensuring robust security and optimal performance.
In straightforward terms, SASE represents the future path of cybersecurity, seamlessly blending network security with connectivity essentials (like accessing the organization's network) through a cloud-native service without compromising the robust security typically associated with location-based setups.
Understanding SASE
SASE, a term coined by Gartner analysts in 2019, represents a cloud-based architecture merging network and security functions to meet modern enterprises' dynamic secure access needs. Its goal is to offer comprehensive security and connectivity for users, devices, and applications, regardless of their location.
As IT landscapes evolve, traditional network security models relying on on-premises hardware and perimeter-based security struggle to keep up. This inefficiency is particularly evident in cloud adoption, remote work, and the proliferation of mobile devices. These challenges demand a more adaptable and scalable security approach.
SASE rises to the occasion by delivering security and networking capabilities as a cloud-based service. It eliminates the reliance on traditional on-premises hardware and facilitates secure access from any location.
What are the key components of SASE?
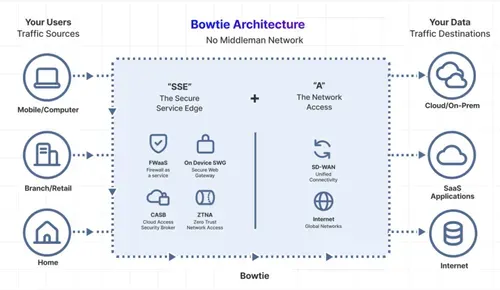
1. Software-Defined Wide Area Network (SD-WAN)
SD-WAN is the foundation of the SASE model, enabling intelligent routing of traffic across multiple networks. It optimizes user experience by dynamically selecting the best paths to the internet, cloud applications, and data centers. SD-WAN simplifies network management, enhances agility, and facilitates rapid deployment of new services across multiple locations.
2. Secure Web Gateway (SWG)
The SWG component of SASE acts as a security barrier between the internal network and the internet. It protects users from malicious web content, cyber threats, and vulnerable websites by enforcing web filtering policies and blocking malware infections, ensuring a secure browsing experience.
3. Cloud Access Security Broker (CASB)
CASBs secure cloud applications and services by enforcing policies that prevent data leaks, malware infections, and regulatory noncompliance. They provide visibility and control over cloud assets, whether hosted in public, private, or SaaS environments, enabling safe and compliant cloud usage.
4. Firewall as a Service (FWaaS)
FWaaS replaces traditional on-premises firewall appliances with cloud-based solutions that offer advanced Layer 7 and next-generation firewall capabilities. Delivered from the cloud, FWaaS provides access controls, threat prevention, and intrusion detection systems, enhancing security without needing dedicated hardware.
5. Zero Trust Network Access (ZTNA)
ZTNA solutions implement a zero-trust model for remote access, where trust is never assumed and access is granted based on granular policies. By providing secure connectivity for remote users without exposing internal applications to the internet, ZTNA enhances security and mitigates the risk of unauthorized access.
6. Centralized Management
Centralized management binds the various SASE components together, allowing organizations to manage policies, configurations, and security controls from a single console. This unified approach streamlines change control, patch management, and policy enforcement, ensuring consistent security across the organization.
Why SASE Matters
Simplifies WAN Architecture: Historically, WAN architecture has been complex and burdened by various disjointed solutions that have led to inefficiency and high management costs. SASE revolutionizes this landscape by integrating networking and security services into a unified cloud-based platform. This consolidation of SD-WAN, security, and network optimization simplifies operations, minimizes complexity, and boosts overall agility.
Enhanced Security/Integrated Solutions:
Robust security is more critical than ever in today's landscape of constant and evolving cyber threats. Secure access service edge meets this need by seamlessly integrating security features into the network infrastructure. Utilizing advanced methods like Zero Trust models, IAM, and encryption, SASE offers comprehensive protection against various threats while maintaining uninterrupted connectivity for users, regardless of their location or device.
Improved User Experience: SASE leverages ubiquitous cloud services and branch-edge devices to deliver a seamless user experience. By optimizing network architecture and reducing latency, secure access service edge enhances end-to-end connectivity and ensures consistent performance across distributed environments. This improved user experience fosters productivity, collaboration, and innovation within the organization.
Cost-Effectiveness: By consolidating networking and security functions into a single platform, organizations can achieve significant cost savings compared to the traditional approach of managing disparate solutions from multiple vendors. Moreover, the shift towards cloud-native architectures reduces the need for on-premises hardware, further lowering capital expenditure and operational costs.
Scalability/Flexibility: The dynamic nature of business requires network architectures to be agile and scalable. With SASE, organizations gain unparalleled scalability and flexibility, empowering them to quickly scale network and security services to match evolving business demands.
SASE Challenges And Considerations
Integrating with Existing IT Infrastructure:
Transitioning to SASE can be challenging for organizations because their existing IT setups, applications, and workflows rely on legacy architecture. This architecture often has limited flexibility for integrating new technologies. As a result, aligning SASE's cloud-based framework with on-premises systems can be cumbersome, as data governance policies, compliance requirements, and interoperability concerns often arise.
Organizations need to perform a thorough assessment of their existing infrastructure to identify potential friction points. Bowtie's SASE platform excels with its distinctive architecture, prioritizing seamless integration while delivering superior privacy and accelerated speeds.
Choosing the Right SASE Provider:
The SASE landscape is saturated with various providers, each offering distinct features and capabilities. Identifying a provider that aligns with the organization's specific security needs, scalability requirements, and integration capabilities can be incredibly exhausting. Providers often have varying approaches to deployment, management, and policy enforcement, adding another layer of complexity.
It is crucial to select a suitable SASE provider. Look for features such as robust security measures, scalability, and seamless integration capabilities. Bowtie's SASE platform stands out with its unique architecture, ensuring privacy and security while offering faster speeds than traditional solutions. Its API-first approach and ready-to-use Terraform provider facilitate quick and hassle-free deployment.
Managing and Training the Organization:
SASE implementation requires significant organizational change, including adjustments to networking policies, security protocols, and overall infrastructure management. Employees must understand how to navigate the new environment while adhering to enhanced security measures. Additionally, teams need to develop new skills and knowledge to monitor and optimize the SASE solution.
How can organizations better prepare for SASE implementation? Develop a comprehensive training plan to educate staff on best practices, potential risks, and new protocols. Choose a provider whose user-friendly interface simplifies network management and whose networking approach minimizes technical complexity.
Bowtie excels in these areas, offering a simplified management system that facilitates employee onboarding and training, enabling organizations to swiftly adapt to the new environment.
Revolutionize Your Network Security With Bowtie
Bowtie stands out as a beacon of innovation and simplicity in the ever-evolving cybersecurity landscape. As enterprises grapple with the complexities of Security Access Service Edge (SASE) implementation, Bowtie offers a streamlined solution that redefines network security.
Bowtie's unique SASE architecture prioritizes privacy and security while also enhancing speed. Unlike traditional cloud-based SaaS solutions, Bowtie's platform delivers faster performance, ensuring your data remains secure without sacrificing efficiency.
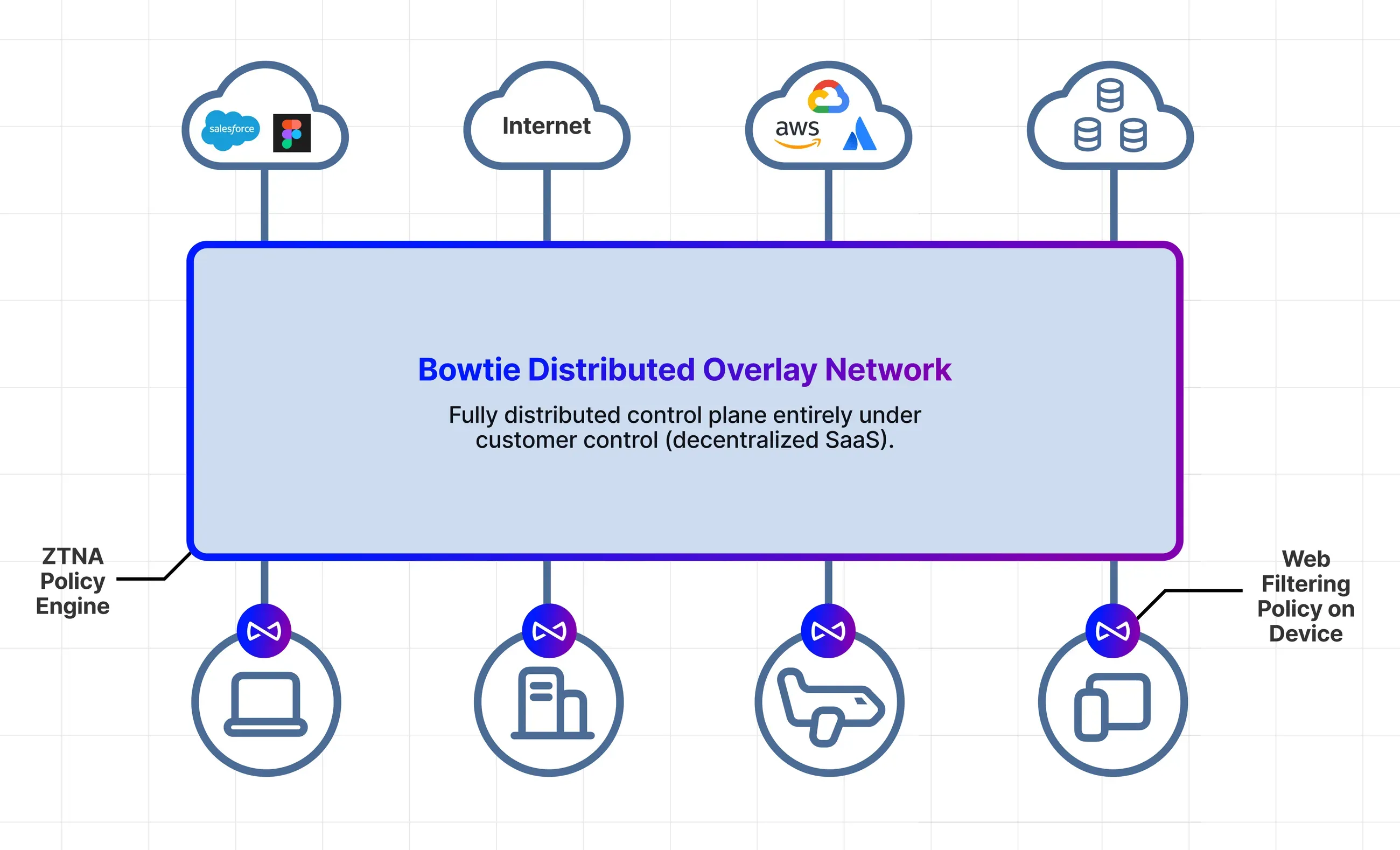
Bowtie makes deployment a breeze with an API-first approach and a ready-to-use Terraform provider. Whether you're migrating from legacy systems or adopting SASE for the first time, Bowtie's platform ensures a quick and seamless transition, minimizing downtime and disruptions.
Bowtie's approach to networking is unparalleled in its simplicity. By creating an overlay network, Bowtie enables seamless communication between devices and private networks, even in cases of overlapping networks. Fast and encrypted direct connections not only enhance security but also optimize performance, reducing the attack surface and ensuring uninterrupted operations.
Ready to revolutionize your network security? Contact Bowtie today to book a demo and discover how our platform can seamlessly integrate with your security program. With Bowtie, navigating the complexities of network security has never been easier.






