Bowtie introduces HTTPS WebSocket tunneling to ensure robust, compliant, and discreet network connectivity – no matter how restrictive your operating environment.
Blog
Trust in vendors to prioritize customer security over their own success is misplaced. Creating expensive, incompatible duplicates of popular products for ‘discerning’ customers discredits the vendor’s security commitment to its broader customer base and balkanizes feature sets.
Fast Flux is a DNS-based evasion tactic that breaks IP blocklists. We unpack how attackers use it to stay ahead and why conventional SASE tools can’t keep up — then show how Bowtie neutralizes Fast Flux with DNS-layer enforcement and decentralized control.
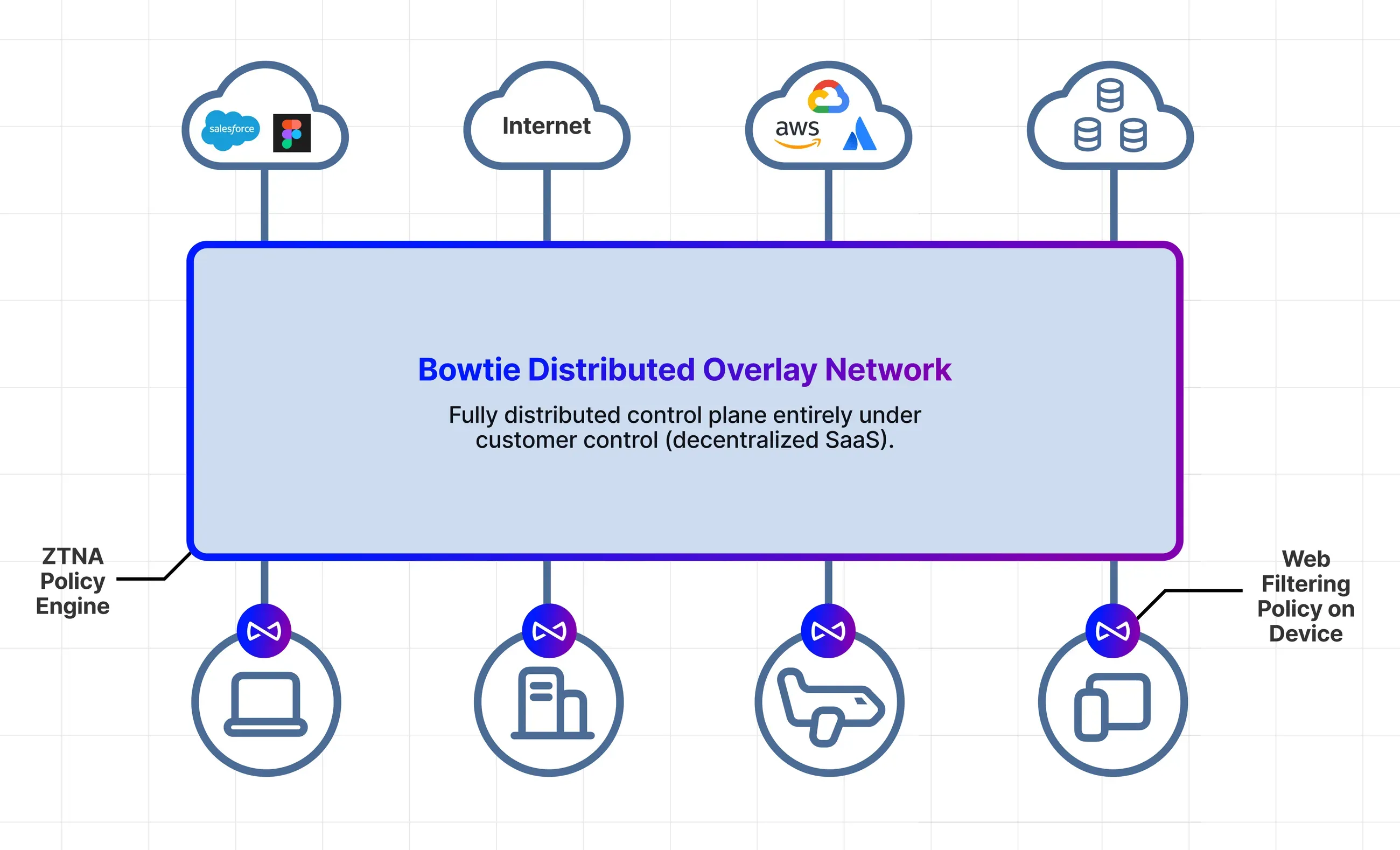
Understanding Sovereign SASE, its benefits and primary deployment components. Learn how Sovereign SASE can help you manage data security and third-party risk, and how Bowtie was built this way from the ground up.
The Digital Operational Resilience Act (DORA) mandates that EU financial institutions strengthen their IT resilience by January 17, 2025. With the deadline imminent, organizations must act now to ensure compliance and secure their operations.
Zero Trust Network Access (ZTNA) is a modern security framework designed to address the complexities of today's digital environments, including remote work, cloud computing, and mobile devices. Read our in-depth guide to ZTNA here.
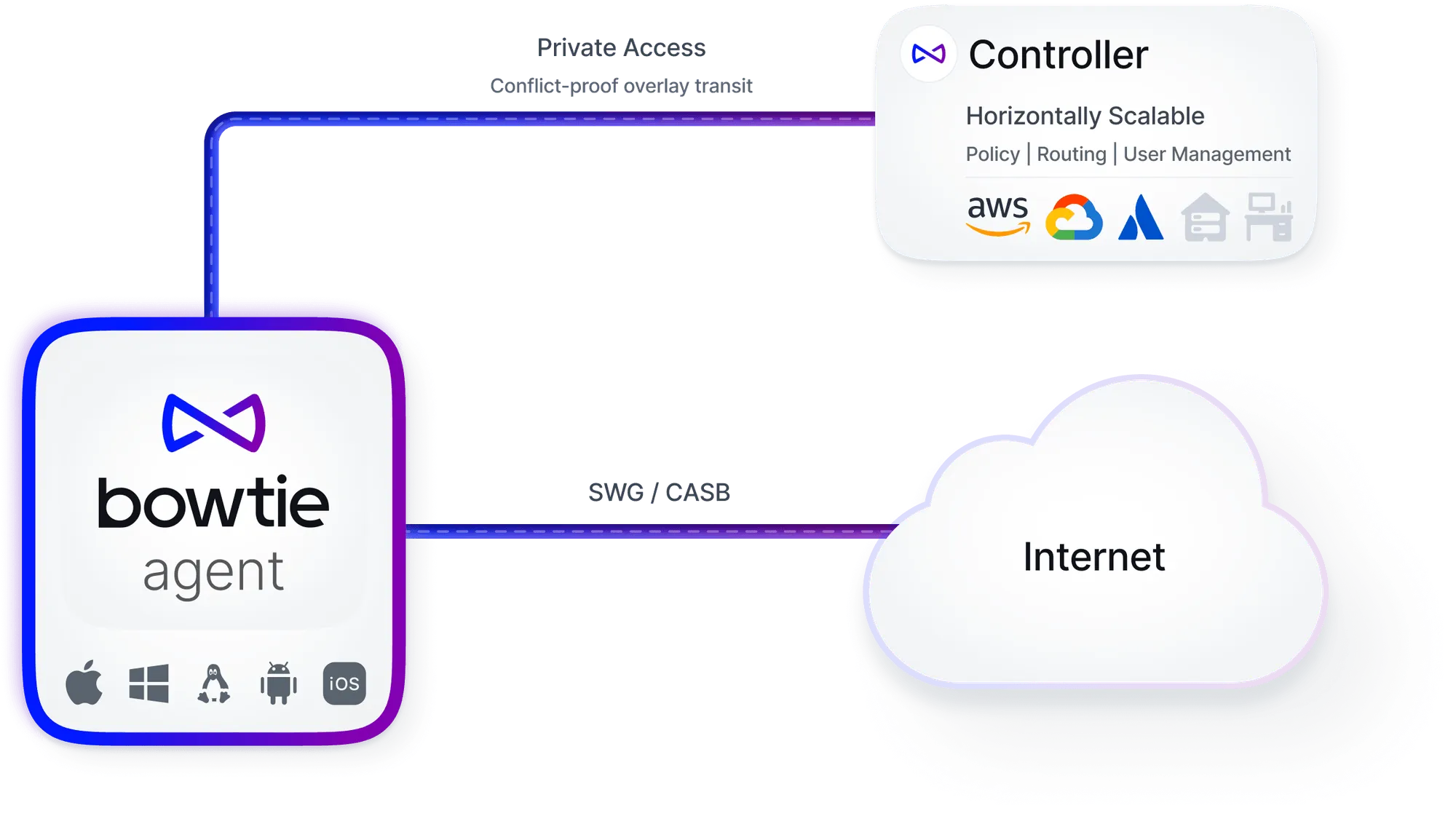
A look at how Bowtie's unique architecture and design helps make network conflicts, network sprawl, and challenges associated with RFC 1918 a thing of the past.
Bowtie's innovative architecture empowers businesses to access private resources without being in the middle of the process. This detailed post is the first in a series on our control plane, first delving into our use of Automerge—a 'Local First' conflict-free data type implementation. Discover how Bowtie achieves resilient, scalable, and partition-tolerant networking, facilitating seamless and efficient integration across multiple sites.
SASE: Secure Access Service Edge. What is it, why does it matter, and how does Bowtie fit into the puzzle?
The industry is hurtling towards the SaaSification of everything, but what does this mean for customers and vendors alike? This in-depth post explores the complex landscape of SaaS, highlighting both its promises and costs, especially in areas like security and autonomy. Through real examples and historical security failures, we suggest a more critical approach to embracing the SaaS model.
Learn how Bowtie uses Nix to build network appliance images, enabling us to support a variety of formats with a high degree of code reuse and an elegant upgrade process. Ensuring that network appliances are easy to run, test, update, and operate reliably is important and underpins Bowtie’s commitment to robust simplicity.
There is a better way to build enterprise networks. Bowtie is building for this future. The network is everywhere now.
The who, what, and why of Bowtie. Mostly the why.
Built for CISOs.
Loved by engineers.
Trusted by Ops
Ready to unify and harden your missions stack?














.avif)



